Local linux login with yubikey u2f & google authenticator 2fa
Sup all,
I have written separate articles about this before but decided to put this all together into one article cause why not.
The purpose of this article is to have google 2fa & yubikey u2f at the login prompt (assuming you do not have a login manager (i don’t)).
This article is gentoo heavy. The equivalent for other distros should not be too different or difficult to figure out.
Needed files
First lets emerge the proper packages (some of these are just in case emerges for future usage):
app-crypt/libu2f-host
app-crypt/libu2f-server
sys-auth/pam_u2f
app-crypt/yubikey-manager
app-crypt/yubikey-neo-manager
dev-python/yubiotp
sys-auth/libyubikey
sys-auth/pam_yubico
sys-auth/yubikey-personalization-gui
sys-auth/google-authenticator
For the Yubikey u2f
Using the yubikey-personalization-gui, make sure that in slot one of the keys you have it configured to OTP. slot 2 can be whatever.
once this is done we have to generate the
${HOME}/.config/Yubico/u2f_keys by running this :sudo pamu2fcfg -u $(logname) >> ${HOME}/.config/Yubico/u2f_keys
if you are using multiple yubikeys, then every time you run the above command, you need to edit file like so:
when you run sudo pamu2fcfg -u $(logname) >> ${HOME}/.config/Yubico/u2f_keys
it will add the data like so :
<username1>:<KeyHandle1>,<UserKey1>:<KeyHandle2>,<UserKey2>:...
<username2>:<KeyHandle1>,<UserKey1>:<KeyHandle2>,<UserKey2>:...
but if you see something like this:
<username1>:<KeyHandle1>,<UserKey1>
<username1>:<KeyHandle2>,<UserKey2>
<username1>:<KeyHandle3>,<UserKey3>
<username4>:<KeyHandle4>,<UserKey4>
then edit so that it looks like the first example or else your u2f will not work and give really weird errors
Now, lets add and edit the pam files:
create file /etc/pam.d/yubico
and add this:
auth required pam_u2f.so cue interactive
these items can be decoded here
and now edit /etc/pam.d/login
and add this line to the top:
auth include yubico
Now lets test that the yubikey u2f is working before fully login out.
press alt+ctrl+f2 to bring you to a tty and you should see the u2f options here.
if this is working, lets move on to the google 2fa portion.
For the Google 2fa
Lets run:
google-authenticatorwhich will look like this:
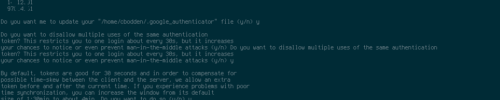
click to enlarge
and just follow the on screen steps which includes using the link provided to add the 2fa portion to your authenticator app.
now lets create file /etc/pam.d/google-authenticator
and add this:
auth required pam_google_authenticator.so nullok
which can be decoded here
and now edit /etc/pam.d/login
and add this line to the top:
auth include google-authenticator
Now lets test that the google 2fa is working before fully login out.
press alt+ctrl+f2 to bring you to a tty and you should see the 2fa options here.
it this is working then you should now have 2fa & u2f login setup.
Notes
I will eventually write articles on:
Again, like with any article, YMMV.
Here is a pic of the yubikeys i tested with:

click to enlarge
Leave a Reply